PEOPLE
Clear roles & secure habits
Least-privilege, approvals that stick, and nudges that make the safe path the easy path.
We translate policy into day-to-day behavior, controls, and evidence—backed by monitoring, rehearsed response, and continuous hardening.
PEOPLE
Least-privilege, approvals that stick, and nudges that make the safe path the easy path.
PROCESS
Join-move-leave, change management, release hygiene, key & vendor handling — actually run.
TECHNOLOGY
Baselines across cloud, endpoints, SaaS, network & blockchain; tuned alerts, less noise.

Interviews + observation to map crown jewels, real workflows, and risks — then a 60-day plan.
24/7 visibility with rehearsed playbooks for on-chain and off-chain events.
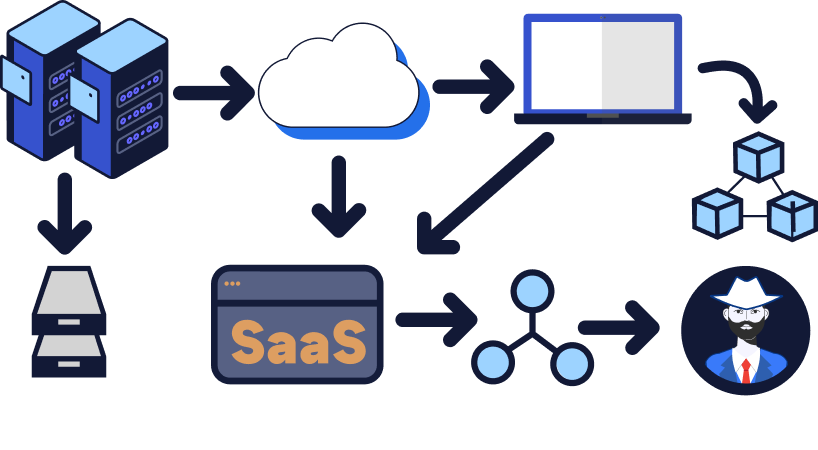
Actionable pipelines across servers, cloud, SaaS, endpoints, network, blockchain, TI.

Practice-based training with real incidents and role-specific scenarios.

Guardrails in CI/CD, secrets & supply chain hardening—keep builders fast and safe.
Fewer routes to critical actions; stronger approvals and key handling.

Lower security toil; clearer signals and faster incident response.
Audit-ready evidence mapped to ISO/SOC2 without busywork.

A backlog the team believes in—and works through.